A PROPOSAL FOR SECURITY PROTOCOL ELEMENTS BETWEEN THE PUBLISHER AND THE PRINTING WORKS IN THE XML TEHNOLOGY ENVIRONMENT
Vilko Žiljak, Mario Barišić, Klaudio Pap, Marinko Žagar
Abstract
: Transfer of important documents or document parts between the publisher and the printing works through the public network Internet may be protected by some of the known tools such as Pretty Good Privacy (PGP) or Secure Multipurpose Internet Mail Extensions /S/MINME). In the same manner open communication between the said participants may be protected with some of the well-known protocols: Transport Layer Security (TLS), Secure Sockets Layer (SSL) or IP Secure (IPSEC).The specific security elements in case of the listed protocols is that cryptic protection is made on the level of the whole document or the whole document is encrypted by passing through the protected link. XML is becoming the standard in the publishing and printing environment and in order to simplify application and the system’s flexibility it is necessary to create a system based on XML. By implementing the XML digital signature (XMLDSIG) for authentication purposes, the XML technology would be applied in the security system. Besides being applied on the level of the whole document for authentication purposes, the XML digital signature may be applied to certain parts of the document so that the users, depending on the authorization level, may have insight into the approved document parts. This paper proposes how to implement XMLDSIG into the computer communication system of the publisher and the printing works2. Digitalno tiskarstvo
Keywords
: XML, digital signature, security, publishing
1. Introduction
The goal of any business communication through the Internet is to provide reliable, confidential, authentic and safe computer communication through several safety elements:
Identity Authentication
Authorization based on authentication
Privacy
Data integrity
Identity Authentication
Each participant in network communication must be absolutely certain that the identity of the other participant in communication is true. On the other hand, the identity of the participants must be hidden from the other participants of the network. In order to prove the participants’ identity, the process of authentication is carried out. It takes place before a participant is allowed to access network resources in order to prevent unauthorized access to resources. The authentication procedure is carried out in two steps. The first step aims at identification, and the second step is to prove the participant’s identity. Identification is registering of the user into the system by his password and login authentication, and identity proving may be one-way or two-way. One-way identity verifying is carried out when one user verifies the other one, and two-way verification is when the users verify one another. There are three types of authentication accesses:
a.
Proof by knowledge where checked information is known only by the authorized user, as for instance the password
b.
Proof by possession when the user must provide an object possessed only by the authorized user, as for instance tokens, credit cards, and similar
c.
Proof by property is a procedure of measuring certain physical properties possessed by the person requesting authorization, such as for instance, the image of the iris, voice and similar.
Practice has proven that the most widely spread authentication system is the proof by knowledge system because it is the oldest one, whereas nowadays there is an increase of proof by property system implementation. A widely used authentication system is the combination of the proof by knowledge and the proof by property systems. In practice this is the case with Automated Teller Machines where besides possessing the necessary credit card one needs to know the PIN code as additional proof.
Authorization based on Authentication
Authorization based on authentication is the reply whereby one participant in communication gives the other party the right to access certain data. Authorization is carried out with the help of one or two systems, Access Control List or Capabilities List.The Access Control List as a way of authorization procedure is a mechanism found in the computer or server where certain procedures are carried out. The system administrator who gives certain rights to the authorized users in such a way that some users have more rights and the other ones have fewer rights maintains the Access Control List. This is manifested in such a way that some users may have insight into some sites, for instance on the web server, whereas others have the right to alter the contents as well. The Access Control List is valid only for the server it was made for and only for the already authenticated users. The Capabilities List is created and administered in the central computer within the public key infrastructure. Afterwards this list may be transferred to a computer within the infrastructure that requires the Capabilities List in order for certain users to have the authorization. This system is called the digital certificate. A digital certificate authenticates a certain user, and on presentation authorizes him as well.
Confidentiality
Confidentiality or secrecy is a characteristic by which only authenticated and authorized users may have insight into data. Data that is the subject of communication cannot be seen, as it is invisible, i.e. encrypted. Encryption is done with fast symmetric algorithms. Data is encrypted only while going through the network, and afterwards it is decrypted. We can observe an example of privacy in the standard way of communication by mail and letters. The sender does not wish anyone to see his message and he will send it in an envelope hiding the written text instead of sending an open-to-all postcard. When the envelope is opened, the receiver can read the message.
Data Integrity
Data integrity is a very important characteristic guaranteeing that the data contents have not been altered. When the message is sent through electronic mail, all communication participants must be completely sure that the received message is the same one that had been sent, i.e. they must be certain that no changes have been made in the message. An effective measure is the use of cryptography and its hashing function. A hash function with its use of a certain algorithm and the message context forms a unique message number. The message number is then sent to the user together with the message. The same hash function is then used to give the message number that is then compared with the number received with the message. In case the numbers are the same, the message has arrived in its initial form.
Undeniability
The participation of a communication participant cannot be denied, i.e. it is possible to prove the participation in communication and this is the meaning of this characteristic. A message having a digital signature is undeniable, and the technique of one-way functions is also used for a digital signature
|
Security Elements
|
Security Goal
|
Technique
|
|
Authentication
|
Source Proof
|
Digital Signature
Challenge – Replay
Password
Biometric units device
|
|
Authorization
|
Access to Authorized Persons
|
Fire Wall
Password
Biometric device
|
|
Confidentiality
|
Message Privacy or Secrecy
|
Cryptographic Protection
|
|
Data Integrity
|
Impossibility of Message Altering
|
Hash function
|
|
Non-leakage
|
Impossibility of Message Sending or Receiving Denial
|
Digital Signature
Digital Certificate
Time Seal
Proof service
|
2. Digital Signature
After mutual identity determination, communication partners begin to exchange messages. However, it is not certain that all messages are coming from the user who is claiming that he is the message sender. Someone may give a false identity because it is not difficult to counterfeit the heading of a document or user data going along with messages, and this is a very simple way to get hold of data that do not belong to a person. The solution lies in the authentication of messages by use of digital signatures. A computer digital signature has the same function as a regular signature, with the difference being in the fact that one person may have one natural signature, whereas one may have several digital signatures. This depends on the digital signature goal. This digital signature may be compared to a seal that we use depending on the intentions. A digital signature used for documents confirms the authenticity, undeniability and authenticity of data in the document. When talking about authenticity, a digital signature is much harder to counterfeit than an ordinary signature. In respect to the different possibilities of digital signatures and access to the message keys, there are the following signatures:
-
Digital signature with a secret key
-
Digital signature with a public key
-
Digital key along with a message abstract
Digital Signature with Secret Key
When using digital signatures with secret keys the whole process goes through a public authority that has the central position where all signatures are stored. A message signed with a secret key first arrives to the central server, and after the secret key is checked, the message is sent to the requested address. The very participation of an intermediary in the communication between two users is not safe as to security reasons, because the central server may read all the messages.
Digital Signatures with a Public Key
A digital signature with a public key is a model for sending messages encrypted by the sender with his secret key and then with the public key of the recipient. The recipient decrypts the message with his secret key, and then checks the message’s authenticity and origin. The favorable side of this model is that only the person possessing the secret key that is in compliance with the public key of the person to whom the message is addressed may read the message.
A digital signature of a message abstract
Combining unique user marks such as a private key possessed by no one except the user and something that is unique for the said document that is signed produces a message abstract digital key. The unique document mark is the message number obtained through application of the one-way SHA function. The one-way SHA function takes the variable message length, no matter what the message size is, and turns it into a 160-bit message number. The message number and the private key both create the signature on the message. The procedure is made in such a manner that someone’s signature may be put on another message because the digital signature verification will not be good and error signs will be received warning the recipient that the message had been changed and that the signature was not the right one. Also, by altering one sign in the document the message number will not stay the same and checking will be negative.
A message signed with a digital signature of the abstract may be sent in readable form or it may be encrypted and this is additional message protection. Encryption of the message in this case is with the sender’s secret key, and the decryption is done with the sender’s public key.
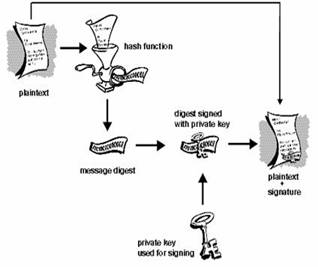
Picture 1. A digital signature of a message abstract
Communication channel security may be provided with some standard technologies on the Internet such as document encryption programs or content encryption protocols when the contents pass through communication channels. Some of the content protecting and authenticating programs are Pretty good privacy (PGP) and Secure Multipurpose Internet Mail Extensions (S/MIME). The use of the listed programs in the XML environment requires additional mechanisms that are not the XML standard.
The protocols for content protection between two communication participants are Transport Layer Security (TLS), Secure Sockets Layer and IP Security (IPSEC). The listed protocols protect the contents while they are in the communication channel in such a manner that they make an overall encryption of it and after passing through the protected channel the contents are completely open, i.e. visible in such a way that they may be sent to a third party. As all the systems tend towards being simple in making and application, so do XML technology based systems tend towards having protection based on XML mechanisms. XML protection mechanisms may provide authentication, authorization and confidentiality for communication participants.
XML based protection mechanisms are:
-
XML Encryption (XMLENC)
-
XML Digital Signature (XMLDISG)
The listed mechanisms should be used in communication between the publisher and the printing works. Documents exchanged between the printing works and the publisher having certain parts that contain confidential business secrets should be protected with one of the XML protection mechanisms.
3.
XML Encryption – Protection Element in the Field of Publishing
An XML document may be protected with one of the listed encryption programs or may be sent through a protected channel. XML encryption may be used in combination with the listed programs and protocols or independently and thus it provides all the known protection elements in the best way. XML encryption provides the possibility of secrecy, integrity protection of a message through message digest, authentication and undeniability of a digital signature.
The XML encryption provides an additional possibility and this is to protect certain parts of documents with different levels of protection. As the XML document represents a clean text and is fully readable, different algorithms, depending on the recipients and their authorities, may carry out encryption of the document’s various parts. The following example will demonstrate how a standard document for the order of a new edition of a previously published matter may be protected when being transferred from the publisher to the printing works in respect to some data that are business secrets (Picture 2). In this document the retail product price will be protected.

Picture 2. The Repeated Edition Order
|
<?xml version="1.0" encoding="UTF-8" ?>
- <dataroot xmlns:od="urn:schemas-microsoft-com:officedata" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xsi:noNamespaceSchemaLocation="010112.xsd">
- <NARUDZBA_PONOVLJENOG_IZDANJA>
<PRODAJA_2003>7034</PRODAJA_2003>
<DEVIZNA_PROD_2003>-35</DEVIZNA_PROD_2003>
…
<Opred_2002>7414</Opred_2002>
<Opred_2003>7316</Opred_2003>
<MPC>48</MPC>
<Rabat>15</Rabat>
</NARUDZBA_PONOVLJENOG_IZDANJA>
</dataroot>
|
|
2.
<?xml version="1.0" encoding="UTF-8" ?>
- <dataroot xmlns:od="urn:schemas-microsoft-com:officedata" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xsi:noNamespaceSchemaLocation="010112.xsd">
- <NARUDZBA_PONOVLJENOG_IZDANJA>
<PRODAJA_2003>7034</PRODAJA_2003>
<DEVIZNA_PROD_2003>-35</DEVIZNA_PROD_2003>
…
<Opred_2002>7414</Opred_2002>
<Opred_2003> 7316</Opred_2003>
<MPC>
<EncryptedData xmlns=’http://www.w3.org/2001/04/xmlenc#’ Type=’http//www.w3.org/2001/04/xmlenc#Content'>
<CipherData>
<CipherValue>A234G6Z7</CipherValue>
</CipherData>
</EncryptedData>
</MPC>
<Rabat>15</Rabat>
</NARUDZBA_PONOVLJENOG_IZDANJA>
</dataroot>
|
|
3.
<?xml version="1.0" encoding="UTF-8" ?>
- <dataroot xmlns:od="urn:schemas-microsoft-com:officedata" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xsi:noNamespaceSchemaLocation="010112.xsd">
- <NARUDZBA_PONOVLJENOG_IZDANJA>
<PRODAJA_2003>7034</PRODAJA_2003>
<DEVIZNA_PROD_2003>-35</DEVIZNA_PROD_2003>
…
<Opred_2002>7414</Opred_2002>
<Opred_2003> 7316</Opred_2003>
<EncryptedData Type=’http://www.w3.org/2001/04/xmlenc#Element’ xmlns=’http//www.w3.org/2001/04/xmlenc#'>
<CipherData>
<CipherValue>A234G6Z7</CipherValue>
</CipherData>
</EncryptedData>
<Rabat>15</Rabat>
</NARUDZBA_PONOVLJENOG_IZDANJA>
</dataroot>
|
Picture 3. The XML Display of the Document Entitled The Repeated Edition Order (1) with the encrypted amount of the retail price MPC (2.) and the encrypted field MPC (3.)
Picture no. 3 point 1 shows the XML document entitled
The Repeated Edition Order where the retail price is found under the <MPC> element. Part 2 shows this same XML document where and XML shell was added within the MPC element replacing the retail price with its code value. Part 3 shows an XML version where a whole element is replaced with an XML encryption program. The advantage of this version in respect to the previous one is that one cannot see what is being encrypted, and this is additional protection
4. The Digital XML Signature
The differences in an XML document that may be created because documents had been made in different systems (parsers) are not usually significant. The differences appear in the form of various line delimiters, empty tracks, comment presentation, etc. However, a difference that may be no more than a single letter or empty space sign may give completely different results when using the hash algorithm to create the number of a message. In this way a document’s integrity is ruined and the document created on basis of different systems no longer complies with the source.
The Canonical XML specification (W3C Recommendation V 1.0) describes the method of generating the document’s physical presentation, named as canonical form. This means that if two documents have the same canonical form, we consider them as the same document. This is very important when applying the XML digital signature, in order to avoid unwanted situations when applying different XML document parsers. The digital signature and the message number (message digest) must be created on the canonical form of the XML document.
There are two types of digital signatures, depending on their position:
-
Enveloped signature-the XML signature is in the same documents with the data Picture 4.
-
Detached signature – data is separated from the XML signature Picture 5.
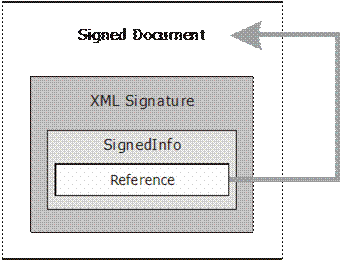
Picture 4. Enveloped Digital Signature
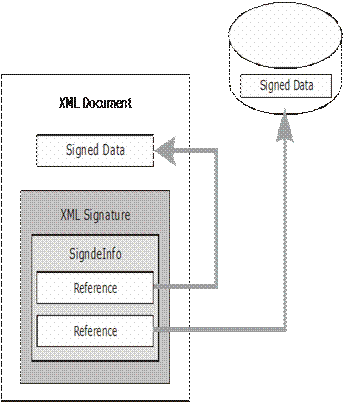
Picture 5. Detached Digital Signature
|
<Signature>
<SignedInfo>
(CanonicalizationMethod)
(SignatureMethod)
(<Reference (URI=)? >
(Transforms)?
(DigestMethod)
(DigestValue)
</Reference>)+
</SignedInfo>
(SignatureValue)
(KeyInfo)?
(Object)*
</Signature>
|
Picture 6. Detached Digital Signature
|
<?xml version="1.0" encoding="UTF-8" ?>
- <dataroot xmlns:od="urn:schemas-microsoft-com:officedata" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xsi:noNamespaceSchemaLocation="010112.xsd">
- <NARUDZBA_PONOVLJENOG_IZDANJA>
<PRODAJA_2003>7034</PRODAJA_2003>
<DEVIZNA_PROD_2003>-35</DEVIZNA_PROD_2003>
…
<Opred_2002>7414</Opred_2002>
<Opred_2003>7316</Opred_2003>
<MPC>48</MPC>
<Rabat>15</Rabat>
</NARUDZBA_PONOVLJENOG_IZDANJA>
</dataroot>
|
|
2.
<Signature xmlns="http://www.w3.org/2000/09/xmldsig#">
<SignedInfo>
...
<Reference URI="#NARUDZBA_PONOVLJENOG_IZDANJA">
<Transforms>
<Transform Algorithm="http://www.w3.org/2001/04/xmlenc#decryption">
<DataReference URI="#enc1"
xmlns="http://www.w3.org/2001/04/xmlenc#"/>
</Transform>
<Transform Algorithm="http://www.w3.org/TR/2000/
CR-xml-c14n-20001026"/>
</Transforms>
...
</Reference>
</SignedInfo>
<SignatureValue>
...
</SignatureValue>
<Object>
<order Id="NARUDZBA_PONOVLJENOG_IZDANJA">
<PRODAJA_2003>7034</PRODAJA_2003>
<DEVIZNA_PROD_2003>-35</DEVIZNA_PROD_2003>
...
<Opred_2002>7414</Opred_2002>
<Opred_2003>7316</Opred_2003>
<EncryptedData Id="enc1"
xmlns="http://www.w3.org/2001/04/xmlenc#">
...
</EncryptedData>
<Rabat>15</Rabat>
</NARUDZBA_PONOVLJENOG_IZDANJA>
</Object>
</Signature>
|
Picture 7. An Example of a Digitally Signed DocumentEntitled The Repeated Edition Order
Picture 6 shows a proposal for the syntax of the XML digital signature made by the W3C consortium. By using this proposed standard, an XML digital signature protection was created for the document entitled
The Repeated EditionOrder (Picture 7). The data that requires protection is referenced with an element through ID attributes (in our example ID="encl").
6. Conclusion
Process automation and automatic data exchange is a development priority in all graphics and publishing systems. It is very evident now that XML technology will be the “highway” for such processes. There must be protection elements in XML document exchange that must provide authentication, authorization and confidentiality to the communication participants. The XML XML Encryption (XMLENC) and XML Digital Signature (XMLDISG) protection mechanisms have the role to increase the safety in communication on all XML document levels.
This paper gives a proposal for implementing digital signatures in XML documents that are transferred from the publisher and the printing works and vice versa. The XML <signature> above the XML retail price element <MPC> was incorporated into the original unprotected document. In order for the proposed protection to be able to function, the only thing needed is to create a simple program with the user’s interface according to XML elements required to be encrypted.
7. References
[1.]
Barišić, M., Žiljak V. (2003):
XML tehnologija u povezivanju izdavaštva i tiskarstva, Međunarodni simpozij “Ofsetni tisak”, Zagreb
[2.]
Bates, C. (2003):
XML in Theory and Practice,
John Wiley & Sons
[3.]
Blake Dournaee, (February 6, 2002):
XML Security, Osborne/McGraw-Hill; Pitts, N.; In Record Time XML, Sybex
[4.]
Brown, P. (2003): Information Architecture with XML: A Management Strategy, John Wiley & Sons
[5.]
Eastlake Donald E., Kitty Niles, (July 19, 2002):
Secure XML: The New Syntax for Signatures and Encryption, Addison-Wesley Pub Co; 1st edition
[6.]
Žiljak, V. (2003):
Vođenje grafičke proizvodnje XML tehnologijom, Međunarodni simpozij “Ofsetni tisak”, Zagreb
[7.]
http://www.w3.org



